Diskcryptor Portable

What really prompted this post is I discovered native OS encryption isn’t always an option, and the relatively portable solution I used until now (EncFS) doesn’t play well with Windows 8.1. EFS isn’t available in some versions of Windows, and Microsoft forces users to to ‘the cloud’. This is just retarded, given solid home directory and disk encryption have been readily available in most versions of Linux for over a decade. So I had a little problem to solve. Different encryption solutions work in different ways, and are designed for different situations. For example, GPG file encryption is excellent for sending or uploading stuff to online storage, but it’s awkward for data in storage.
Full disk encryption is excellent for protecting drives, but the protection generally isn’t portable. Realistically we’re going to use a combination of two or more solutions. GPG and BleachBit Technically the simplest and safest method for physically transporting files between two machines with different operating systems, but it’s awkward in practice. The problem exists largely because file encryption typically creates an encrypted copy of a file, and the original must be wiped – will simplify this process on Windows. Compare this to EncFS, where no unencrypted data touches persistent storage.
DiskCryptor is an open encryption solution that offers encryption of all disk. The application is completely portable, because due to its light weight it can be.
Volume Encryption with DiskCryptor The first task is to ensure sensitive files aren’t being carried around unencrypted on a laptop’s removable media. One solution I tried was, which takes the place of EFS and BitLocker. The removeable media here is a 16GB storage device, which I already formatted to FAT32 and populated with a handful of test files.
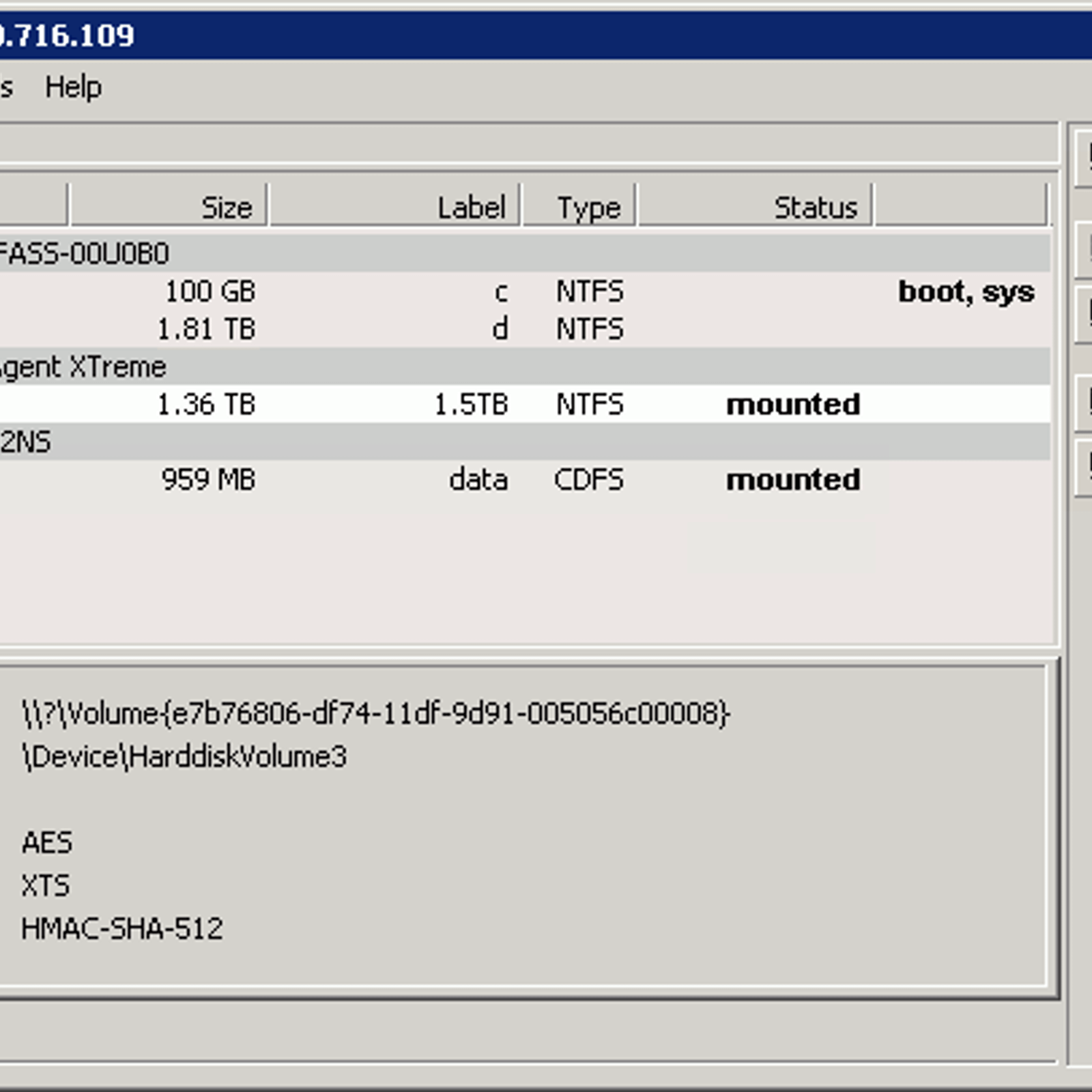
It took over an hour to set up encryption. The DiskCryptor application must be used for decrypting and mounting the volume after this, but it works very fast. Without the application, the volume appears as a blank unformatted partition. The drives on the Windows and Linux machines can be encrypted. Now there’s just the portable USB storage to secure. VeraCrypt Given the TrueCrypt project was discontinued amid the Ed Snowden drama, with commercial privacy solutions (Silent Circle, LavaBit, etc.) also being pulled, it’s understandable that people would feel uneasy about a appearing (especially as binaries on Microsoft’s CodePlex).
Drowning in rain and in forest. Chistij blank pasporta ukraini.
Again, for those who want to trade convenience for a more paranoid solution, GPG and Bleachbit is the way to go, but even then it could be argued the underlying technologies (microcode and compilers) might be compromised. For most cases, VeraCrypt looks pretty good as an alternative to TrueCrypt, but I wonder how long the software will be maintained and whether it is actually safer than TrueCrypt at this point. I decided to try it creating a small 2GB volume and accessing it on both Windows and Linux – and it worked. Setup is fairly straightforward. I recommend using an AES-Twofish (256-bit) cipher combination, with SHA 512.
I also recommend creating the encrypted volumes on a Linux physical machine. Instead of installing VeraCrypt on the Windows system, I extracted the files to create the portable version which I’m hoping would execute and mount the volume on anything running Windows. And here’s the same GUI running in the Linux version: It takes about 30 seconds to decrypt the volume, but it means we have at least a portable method that minimises the chances of anything sensitive being recovered from a lost/stolen device. IStorage datAshure Not necessarily an endorsement, but it’s a hardware-based alternative worth considering if TrueCrypt and EncFS aren’t options, and if you’re prepared to fork £40 for a 4GB drive. The automatically encrypts/decrypts the data while the PIN-protected Hardware Security Module stores the cryptographic key. The hardware is highly tamper-resistant, it wipes the data after a given number of unsuccessful attempts, and according to the manufacturer there is no backdoor.